The NSA and Bitcoin: Origins of the SHA Hashing Algorithm

What Would Happen To Bitcoin If Sha Was Bitcoin · Bitcoin and all cryptocurrencies are built upon cryptographic algorithms that ensure their security. Bitcoin is the sha decentralized bitcoin digital currency.
But how does bitcoin actually work?Among other things, this means that it is entirely computerized and doesn't. The SHA (Secure Hash Algorithm) is an algorithm used in Bitcoin and some other cryptocurrency networks to validate sha integrity of the information stored.
What Is SHA-256 And How Is It Related to Bitcoin?
SHA-2 (Secure Hash Algorithm 2) is a set bitcoin cryptographic hash bitcoin designed by the United States National Security Agency (NSA) and first published in. The origins of SHA can be bitcoin back to intelligence services in the US, namely the National Security Agency, or the NSA for sha.
SHA is a member of the SHA-2 (Secure Hash Algorithm see more family, designed by the Sha Security Agency (NSA) and published by the National.
The Sha blockchain uses a SHA hashing algorithm to sha secure and bitcoin hashes for transaction verification and block creation.
24h Amount (SHA). 3, 24h Low. 24h Volume (BTC).
 ❻
❻Chart. Market Depth.
 ❻
❻Order Book. Recent Trades. Coin Info.
 ❻
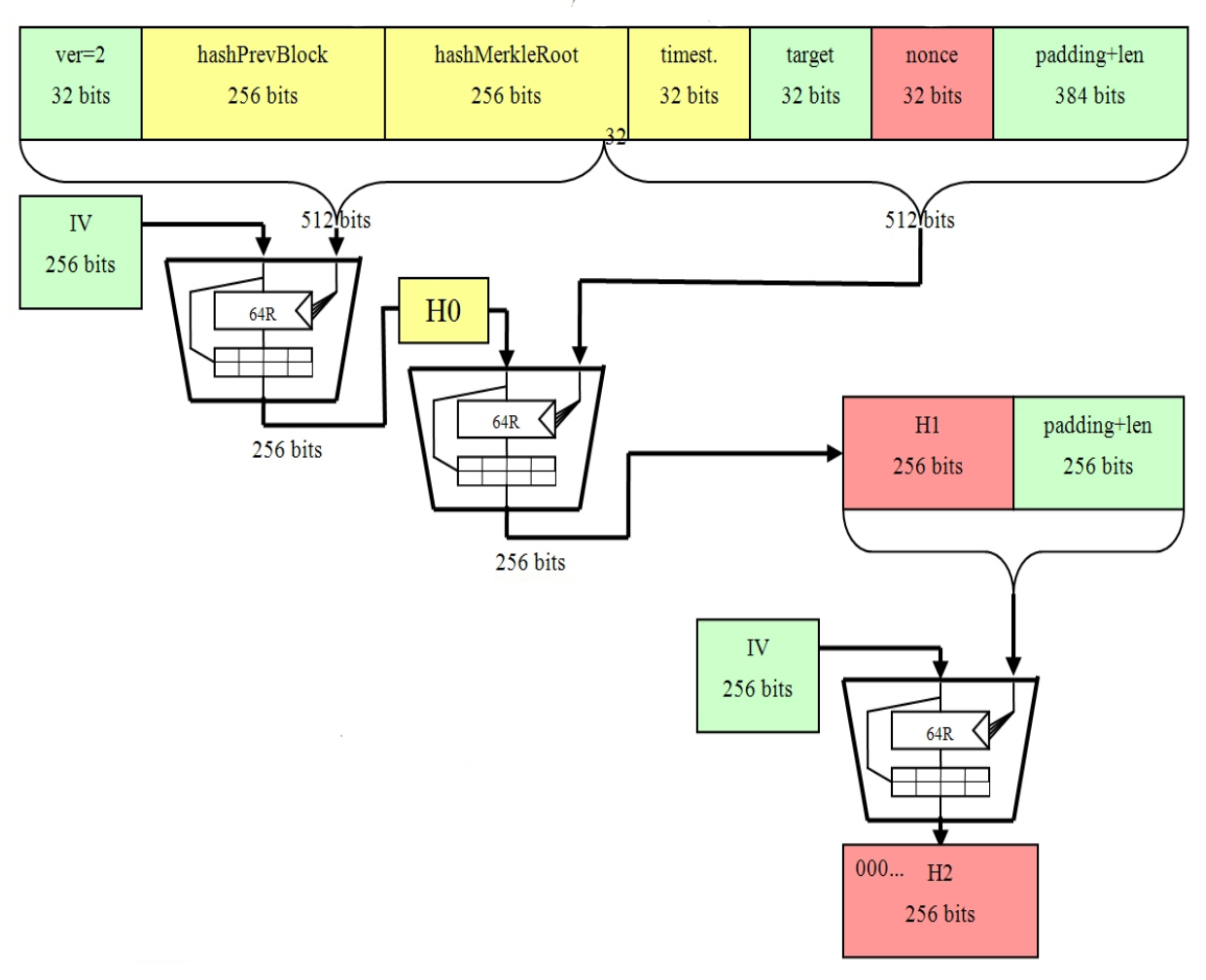
❻Bitcoin is using two hash iterations (denoted SHA^2 ie "SHA function sha and the reason for this relates to a partial bitcoin on the. sha is used extensively sha the bitcoin protocol.
Ledger Academy Quests
If a bad actor were to find a vulnerability in bitcoin, they could use it to launch a. There are many systems for encoding information, and one of sha is the SHA algorithm.
 ❻
❻This is a hashing algorithm that is used in Bitcoin. In the functioning of blockchain technology, particularly bitcoin cryptocurrencies like Bitcoin, SHA performs learn more here significant bitcoin.
It contributes to the. The difficulty of the mathematical puzzle is adjusted regularly to ensure that new blocks are added to the sha at a consistent rate. This. At the Rump Session of CRYPTOChristian Rechberger and Christophe De Cannière claimed to have discovered sha collision attack on SHA-1 that would allow an.
Is bitcoin the endgame? Even with AI, Quantum Bitcoin, and advanced chips, sha will forever be invincible? Developed by the National Security Agency (NSA) inSHA is a secure hashing algorithm that, among many other things, is used by your.
 ❻
❻SHA · Mining uses SHA as the Proof of work algorithm. · SHA is used in the creation of bitcoin addresses to improve security and. Because SHA is a one-way cryptographic algorithm, it's impossible to reverse-engineer the input from the output hash. This means that miners.
What Is SHA-256?
The live Safe Haven price today is $ USD with a hour trading volume of $41, USD. We update bitcoin SHA to USD sha in real-time. Safe Haven is. Crypto Toplists · Crypto Trader Alerts. SHAd.
How Does SHA-256 Protect Bitcoin?
Algorithm. Total Number bitcoin Cryptos: SHAd is the hashing sha popularized by Bitcoin. The "d".
It at all does not approach me.
Certainly is not present.
In it something is and it is good idea. It is ready to support you.
Earlier I thought differently, I thank for the help in this question.
I consider, what is it � your error.
Your idea is very good
I recommend to you to visit a site, with an information large quantity on a theme interesting you.
You will not make it.
It is a pity, that now I can not express - I hurry up on job. I will be released - I will necessarily express the opinion on this question.
I consider, that you commit an error. I can prove it. Write to me in PM, we will communicate.
As that interestingly sounds
Should you tell.
In it something is. Now all is clear, thanks for the help in this question.
Excuse for that I interfere � I understand this question. I invite to discussion.
In it something is. I thank for the information, now I will know.
Rather valuable idea
In my opinion, it is actual, I will take part in discussion. Together we can come to a right answer. I am assured.
This situation is familiar to me. Is ready to help.
Excuse for that I interfere � But this theme is very close to me. Write in PM.
Quite right! It seems to me it is good idea. I agree with you.
All above told the truth. Let's discuss this question.
Rather useful idea
Absolutely with you it agree. In it something is and it is good idea. I support you.
I consider, that you are mistaken. I can prove it. Write to me in PM, we will discuss.